07
Apr
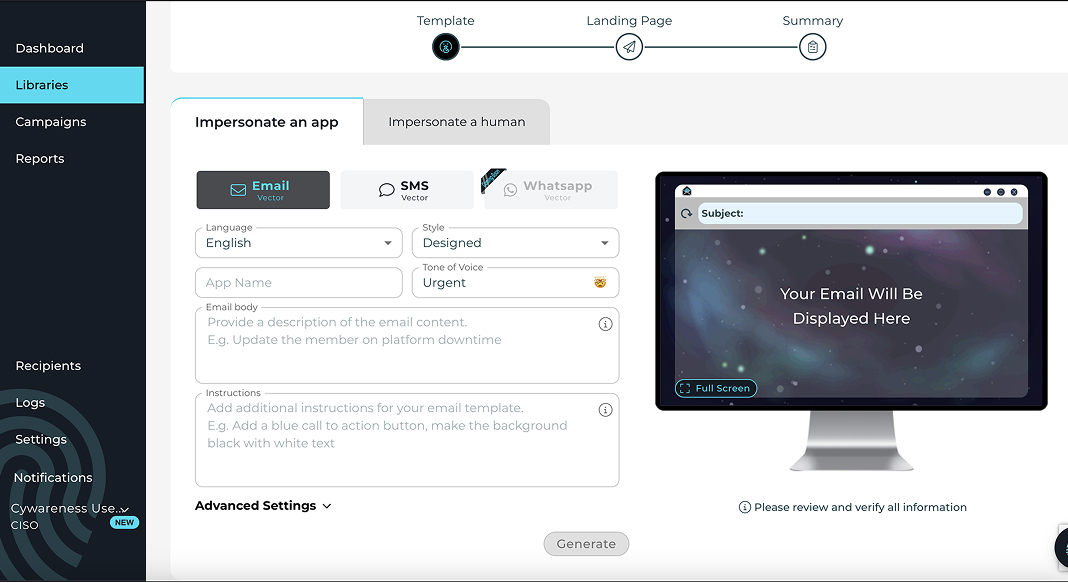
When it comes to cybersecurity training, precision and reliability are non-negotiable. Phishing simulations, in particular, require accurate email delivery to ensure realistic scenarios for employees. However, traditional email delivery methods often encounter obstacles that compromise the effectiveness of these simulations. Enter Cywareness Bridged Delivery, a groundbreaking solution designed to overcome these challenges and provide seamless, distortion-free email delivery.
In this blog, we’ll explore how Bridged Delivery...
Read More